
1. 智能合約存在大量安全隱患
2010年8月,比特幣發生了一次整數溢出漏洞(CVE-2010-5139),使得攻擊者產生了2筆輸出92233720368.5427個比特幣的交易,遠超中本聰設定的2100萬上限。 2018年4月,以太坊上的智能合約也接連發生2起整數溢出漏洞(CVE-2018-10299,CVE-2018-10376),攻擊者憑空增發了大量的token,使得投資者的資產被嚴重稀釋。
為了分析當前最流行的以太坊智能合約的安全性,SECBIT實驗室安全團隊深度掃描檢測了當前正在運行的23357個智能合約源代碼,通過AI智能合約安全審計模型掃描,實驗室安全專家發現其中大量合約代碼存在著不同程度的安全隱患。
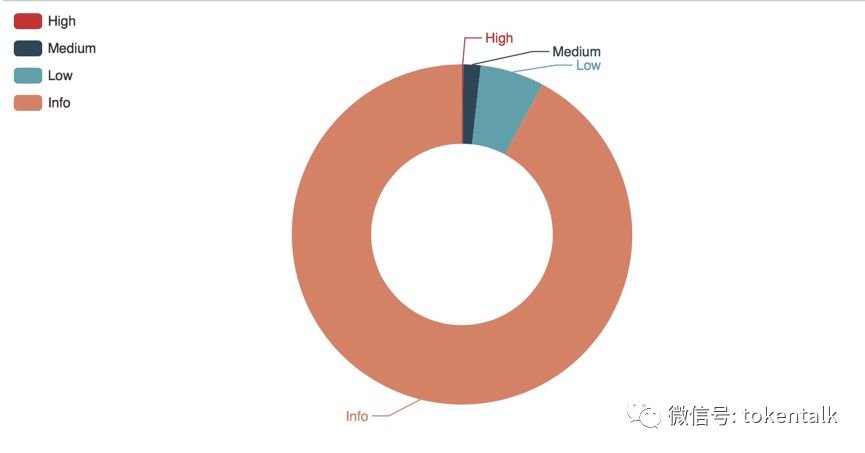
根據掃描結果顯示,這23,357個智能合約源代碼中,智能合約總共出現了405882個不符合安全開發規范的項,平均每個合約有超過17個規范違反項,盡管這些點不會立即導致智能合約出現安全漏洞,但是對于保護巨量數字資產的代碼,這些問題都有可能成為黑客的分析和攻擊方向,作為項目方的開發人員,不能忽視這些隱患,并保持清晰的思路,盡可能嚴格按照安全開發規范要求進行開發,這樣才能避開潛在的攻擊威脅。
掃描結果顯示,低級別(Low)的安全問題有26,821個,主要有未指明版本號以及高GAS消耗等問題。未指明版本號可能會在將來新版本編譯器上遇到不兼容問題。SECBIT實驗室的安全專家建議開發者在開發過程中,為用戶調用函數節約GAS,以避免在網絡擁堵時讓用戶負擔過多手續費。
另外中級(Medium)安全問題有7,202個,主要有整數溢出、除法、依賴時間戳、區塊哈希的運算。整數溢出問題在BEC、SMT的Token發行合約上已經展現出了危害性,在此不再贅述。EVM目前不支持浮點數,除法運算在EVM上表現為向下取整,開發者在智能合約上應當盡量避免,以免發生潛在的安全隱患。另外如果將時間戳、區塊哈希作為隨機數來源,有一定被礦工操縱的風險,開發者應該注意設計安全的交互協議。
掃描結果中高危(high)安全問題有572個,主要集中在代碼重入、短地址攻擊、強制轉賬、使用合約余額來做判斷、高地址臟數據、tx-origin的誤用上。以太坊歷史上曾發生過一次震驚世界的攻擊——the DAOHack,這也是代碼重入漏洞展示威力的一次標志性事件。這些問題都有重演類似嚴重安全事件的可能。
2. 以太坊智能合約信息現狀
除了上文提到的使攻擊者受益的一類安全問題,還有一些類似Parity多重簽名錢包的問題,盡管沒有一方可以獲益,但是用戶卻遭受了巨額的損失。
為了解到當前智能合約的發展現狀,SECBIT實驗室安全團隊監控掃描了以太坊上所有歷史數據,并統計分析了自創世區塊以來,以太坊上所有創建的智能合約信息。
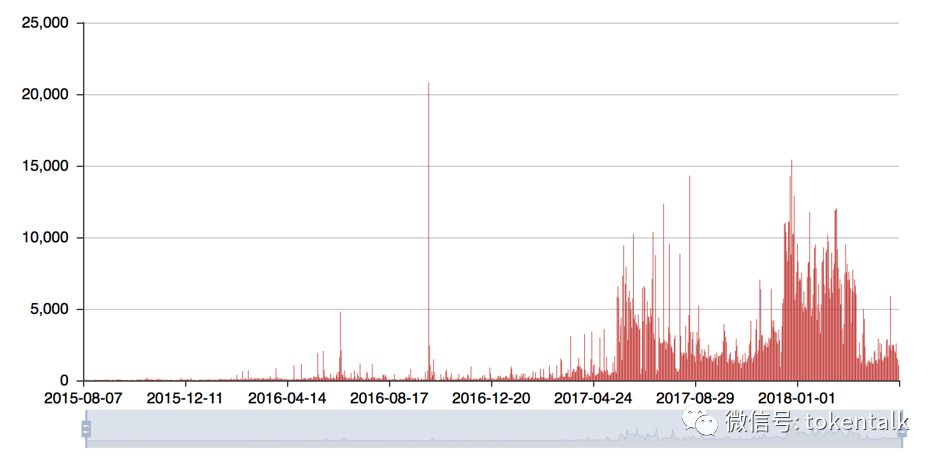
圖中橫軸表示日期,縱軸表示當日智能合約創建數量
如圖所示,以太坊智能合約每日創建數量總體呈現上升趨勢,并且合約代碼的復雜程度也隨之增高 。
據Amberdata網站監控統計,目前以太坊上每小時交易所涉及的金額已經達到1.6億美元,每天可達40億美金,其中53.5%的交易涉及智能合約。隨著智能合約數量的進一步增多,DApp的廣泛應用,其管理的數字資產數量提升,面臨的安全威脅也隨之增長,由于智能合約難以通過傳統的升級、打補丁等方式填補漏洞,通常只能在開發期間或合約部署前進行完備的安全檢查。然而由于一般開發人員的安全意識仍然不夠,可能在開發時無法意識到自己引入了安全隱患,這極有可能給智能合約帶來相當大程度的安全隱患。每一個暴露在開放網絡上的智能合約都有可能成為專業黑客團隊的金礦和攻擊目標。
3. 引入第三方代碼安全審計至關重要
不同于傳統的閉源軟件,區塊鏈上的智能合約代碼是完全公開透明、并且開源的,因此引入代碼安全審計是不可缺少的重要安全舉措,通過第三方專業的審計這才能保證在合約在虛擬機、語言、業務邏輯等多方面的穩定可靠,并具備抵御攻擊能力。作為管理巨量數字資產的智能合約,透過專業的第三方團隊來進行安全審計是保障資產安全的負責任的措施。
據SECBIT智能合約安全審計平臺實時追蹤,現今以太坊上已經部署的合約數量已經達到6,081,658個(統計截止到塊高度為5,460,050),而真正經過第三方安全審計的智能合約數量可能還不足1%,未來隨著智能合約數量的進一步爆發式增長,如果智能合約依然未經安全審計而上鏈運行,區塊鏈安全烏云仍將無法退去。
如需深入了解智能合約安全開發與安全審計的細節,請與SECBIT實驗室聯系:info@secbit.io
SECBIT實驗室 由一群熱愛區塊鏈技術的極客組建,專注于可信智能合約與安全共識協議研究。實驗室成員遍布在全球多個國家,專業領域涉及區塊鏈底層架構、智能合約語言、形式化驗證、密碼學與安全協議、編譯與分析技術、博弈論與加密經濟學等諸多學科。SECBIT實驗室目前著重于研究區塊鏈智能合約的安全問題,助力區塊鏈團隊提高智能合約的可靠性與安全性,開展構建智能合約安全框架的理論探索與技術研發,參與共建共識、可信、有序的區塊鏈經濟體。
(本文由幣須說深度合作伙伴SECBIT研究室提供)
___________英文原版_____________
In August 2010, Bitcoin had an integer overflow vulnerability (CVE-2010-5139), which caused the attacker to generate 2 transactions of 92233720368.54277039 Bitcoins, far exceeding the upper limit of 21 million set by Nakamoto Satoshi.
In April 2018, there were two consecutive integer breaches in the smart contract on Ethereum (CVE-2018-10299, CVE-2018-10376). The attacker issued a large number of tokens out of thin air, causing the investor’s assets to be heavily diluted.
In order to analyze the security of the most popular Ethereum smart contracts, the SECBIT laboratory security team in-depth scan detected the currently running 23,357 smart contract source code. Through the AI smart contract security audit model scan, laboratory security experts found a lot of them. There are different degrees of security risks in the contract code.

According to the scan results, among the 23,357 smart contract source codes, there were a total of 405,882 non-compliant security development items in smart contracts, with an average of more than 17 specification violations per contract, although these points would not immediately lead to smart contracts. There are security vulnerabilities, but for the protection of huge amounts of digital assets code, these problems may become the analysis and attack direction of hackers. As a project developer, you cannot ignore these hidden dangers, and maintain a clear idea, in strict accordance with the security The development specification requires development so that potential attack threats can be avoided.
The scan results showed that there were26,821 low-level security issues, including unspecified version numbers and high GAS consumption. Unspecified version numbers may encounter incompatibility issues in future new version compilers. Security experts at SECBIT Labs advise developers to save GAS for user calls in the development process to avoid overloading users with network congestion.
In addition, there are 7,202 medium security issues, including integer overflow, division, dependent timestamp, and block hash operations. The issue of integer overflow has already shown harm on the Token issue contract of BEC and SMT, and will not be repeated here. EVM currently does not support floating-point numbers, and division operations are rounded down on the EVM. Developers should avoid using smart contracts to avoid potential security risks. In addition, if the timestamp and block hash are used as sources of random numbers, there is a certain risk that the miner will manipulate it. Developers should pay attention to designing a secure interactive protocol.
There are 572 high-security issues in the scan results, mainly focusing on code reentry, short address attacks, forced transfers, use of contract balances for judgment, high-address dirty data, and tx-origin misuse. In Ethereum’s history, there has been an attack that has shocked the world—the DAO Hack. This is also a symbolic event of code reentrance.
All these issues have the potential to repeat similar serious security incidents.
In addition to the type of security issues mentioned above that benefit the attacker, there are some problems similar to the Parity multi-signature wallet. Although none of the parties can benefit, the user suffers huge losses.
In order to understand the current status of the development of smart contracts, the SECBIT laboratory security team has monitored and scanned all Ethereum historical data, and has statistically analyzed information on smart contracts created on Ethereum since the creation .
 As shown in the figure, the daily creationvolume of Ethereum smart contracts shows an overall upward trend, and the complexity of the contract code also increases.
As shown in the figure, the daily creationvolume of Ethereum smart contracts shows an overall upward trend, and the complexity of the contract code also increases.
According to Amberdata website monitoringstatistics, the current hourly price of Ethereata's transactions has reached 160 million U.S. dollars, up to 4 billion U.S. dollars per day, 53.5% of which involve smart contracts. With the further increase in the number of smart contracts, the widespread use of DApp has led to an increase in the number of digital assets it manages and the security threats it faces. With smart contracts, it is difficult to fill loopholes through traditional upgrades and patching. Complete security checks during development or before contract deployment.
However, because the general developer'ssafety awareness is still not enough, it may not be realized at the time of development that he has introduced a security risk, which is very likely to bring a considerable degree of security risks to smart contracts. Every smart contract exposed on an open network can potentially become a goldmine and attack target for professional hacking teams.
Unlike traditional closed source software,the smart contract code on the blockchain is completely open, transparent, and open source. Therefore, the introduction of code security auditing is an indispensable and important security measure. Through a third-party professional audit, this can ensure that the Virtual machines, languages, business logic, and other aspects are stable and reliable, and have the ability to resist attacks. As a smart contract for managing massive digital assets, conducting security audits through professional third-party teams is a responsible measure to ensure the security of assets.
According to the real-time tracking of the SECBIT smart contract security audit platform, the number of contracts already deployed on Ethereum has reached 6,081,658 (statistics block size is 5,460,050), and the number of smart contracts actually undergoing third-party security audit may be less than 1%. In the future, with the further explosive growth in the number of smart contracts, if smart contracts are still running without security audits, the blockchain security cloud will not be able to recede.
For further details on smart contract security development and security audits, please contact SECBIT Labs at info@secbit.io.
________________________________________
SECBIT Labs is formed by a group of geeks who love blockchain technology and focuses on the study of trusted smart contracts and security consensus protocols. Lab members are located in many countries around the world. The areas of expertise include blockchain infrastructure, smart contract language, formal verification, cryptography and security protocols, compilation and analysis technologies, game theory andencryption economics, and many other disciplines. SECBIT Labs currently focuses on the research on the security of blockchain smart contracts, helps blockchain teams improve the reliability and security of smart contracts, conducts theoretical exploration and technology research and development on building smart contract security frameworks, and participates in consensus building. A faithful and orderly blockchain economy.
